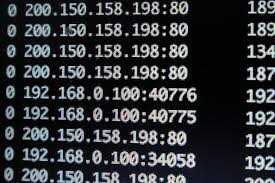
The cibercriminals installed the malware in Linux devices of all types, including Wi-Fi routers and network storage devices, taking advantage of poor passwords used to protect the shell command in Linux devices. Once the attacker access the system, they run a script that downloads and executes the malware and they hide it using rootkit techniques.
One decade ago, such attacks were unthinkable, but as Linux users grow, “cibercriminals see more opportunities infecting it, that’s why we should make an effort to secure and strengthen Linux-based systems”, says Akamai technologies.
Source: www.computerworld.com







0 Comments