
Access virtual desktops in UDS through HTML5
UDS Enterprise incorporates HTML5, among others, as transport and access protocol to both Linux and Windows virtual desktops.

UDS Enterprise incorporates HTML5, among others, as transport and access protocol to both Linux and Windows virtual desktops.

UDS Enterprise 2.0 supports OpenStack as a hypervisor for access and management of virtual desktops, adding a set of advantages and flexibility in terms of transport protocols, authenticators, etc …
The ease of integration, installation, use and access to virtual desktops are other of the benefits that OpenStack incorporates with UDS Enterprise.
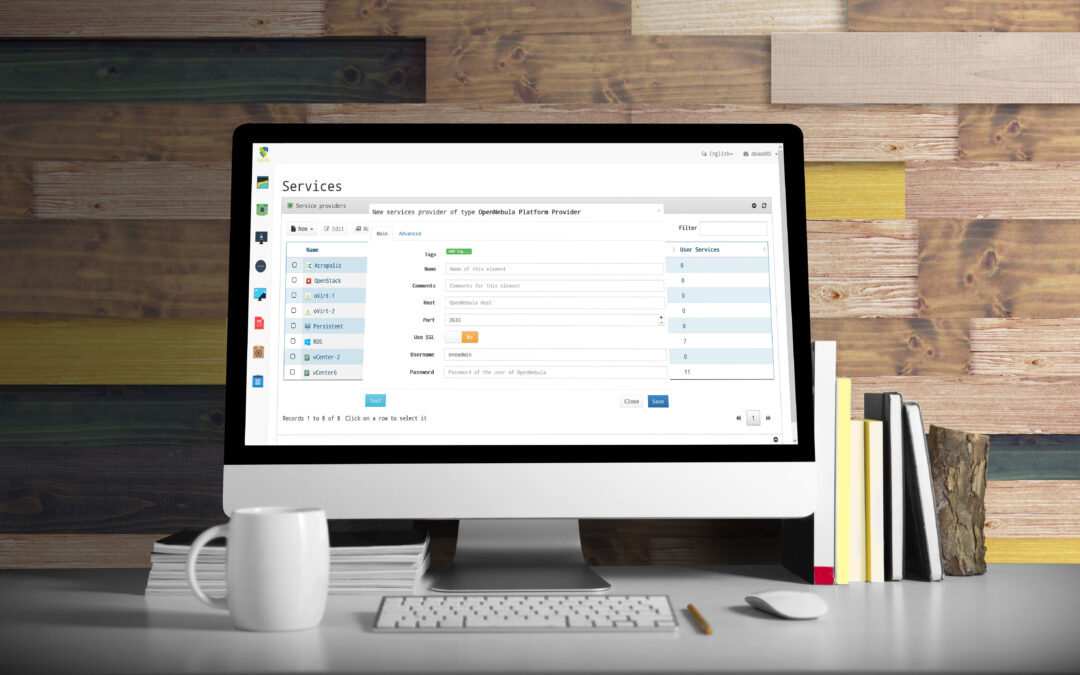
The UDS Enterprise 2.0 VDI connection broker supports OpenNebula as a hypervisor, among others, for accessing and managing Windows and Linux virtual desktops. Among other advantages, UDS Enterprise gives OpenNebula unlimited flexibility by adding support for any virtual hypervisor, authenticator, and connection protocol, and offering the ability to use multiple of these components simultaneously.

Our developers are already working on a new version of our software. One of the most important new features to come with UDS Enterprise 2.1 is the inclusion of two new connection protocols: PCoIP and X2Go.
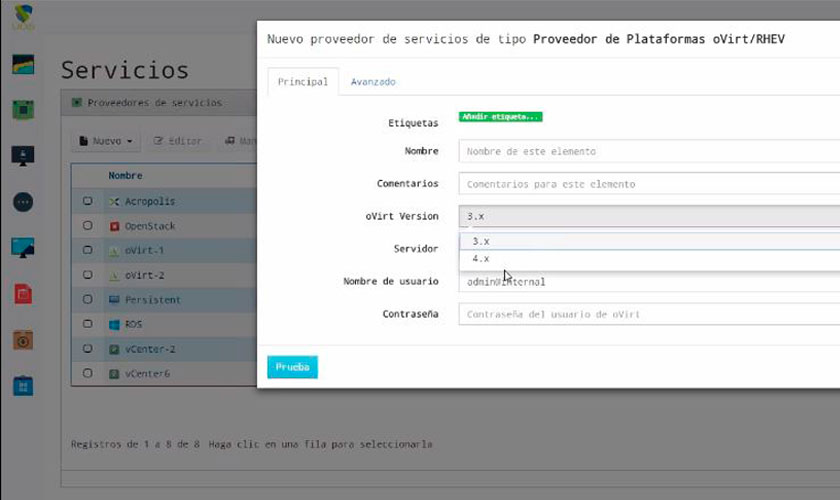
Among the new features included in UDS Enterprise 2.0, he new version of our software that we released in late September, we highlight connectors for new service providers. In addition to the OpenStack and OpenNebula cloud architectures, this new release has a built-in support for oVirt 4.0.